Types of Networks
 WLAN: Wireless Local Area Network (another form of LAN, but with enough specific terms and technology to rate it's own division)
WLAN: Wireless Local Area Network (another form of LAN, but with enough specific terms and technology to rate it's own division)
LAN: Local Area Network (home to office sized networks)
MAN: Metropolitan Area Network (city sized)
WAN: Wide Area Network (country sized)
GAN: Global Area Network (the Internet)
MANs are pretty rare compared to LANs and WANs. I don't know much about them except that they are commonly used to connect one building to another, so I'll just leave MANs out of this. Defining the difference between LANs and WANs is hard enough.
A LAN is loosly defined as an office sized collection of connected computers, but is more like any sized private network, even two shared computers at your house.
A WAN is what is used to connect LANs together, usually over a phone company's network with data circuit and service names like T1, Frame Relay, ISDN, DSL, VPN.
"But wait," you say, "DSL sounds like how I connect from home to the Internet?"
Yeah, it gets hard to divide this stuff when you take a close look. When you connect to the Internet, you are connecting to a WAN, even if it's only temporary, like using a dial up modem, or wirelessly at a Coffee Shop, it's a WAN connection.
The Internet is the utimate WAN, or you can think of it as the system that connects WANs, so folks are starting to call it the GAN. Thinking of "the Internet" as a thing by itself can be confusing because it's really a collection of connected WANs. When you connect to "the Internet" what you are doing entering your Internet Service Providers LAN. You might just be passing through their LAN, to other LANs until you finnally reach your requested destination. Even at work, when connecting to the Internet, what you are doing is passing though your company's LAN, then connecting to or through your company's ISP's LAN, then possbily onto the next LAN until you reach your destination. The stuff that allows you to pass between LANs is a WAN.
Huh? What if the ISP is just a collection of Routers? Is it still a LAN? Well, a router is just a computer with a special function. That function might be running on special hardware, and with special software, but you can turn a standard PC into a Router. What if that wireless coffee shop mentioned above has a server that you can connect to, but they loose their Internet connection? At the moment they loose their Internet connection, you switched from making a a GAN connection (that is a series of WAN connections) to a LAN connection. If you really want to get into it, you could say that the parts of your computer, the Hard Drive, RAM, Processor, CD/DVD/whatnot are all connected together by a network called a system bus.
That's how flimsy these terms are, so just deal with it and lets move on to a break down of what networks are trying to do.
A Network Analogy for the confused
It helps to think of all this network stuff in terms of mailing a letter to a corporation.
To mail something, you put your letter in an envelope, address the envelope, and give it to the postman who gives it to the post office. The post office gets the package to the building's mailbox, then someone takes it from the box and gets it to the right person who reads the letter.
The IP part is like the envelope, it's got the address on it, and your data in it. The letter is like your data.
The carrier is like a network protocol (usually Ethernet), it takes your message to the nearest post office. The post office is like a Router, it takes your package wherever it's addressed to.
The carrier (Ethernet) and the Post Office (Router) don't know what's in the envelope, they just know the address.
The building is like a computer. It's the address destination.
The building's mailroom is like TCP, it recieves all mail then makes sure the mail gets to the right person, in this case the person is the application that will read the data.
TCP sorts the mail by type, letters in one bin, boxes in another bin, etc, so the mail bins are like TCP ports. TCP ports identify what kind of data is comming in and sends that to the right application to be processed (read).
Okay so that's the parts of a transmission: Data, IP, Network, TCP, TCP ports, Application. That's WHAT they do. HOW they do this can be confusing, so try using a simple metaphor if you get confused.
Network Components
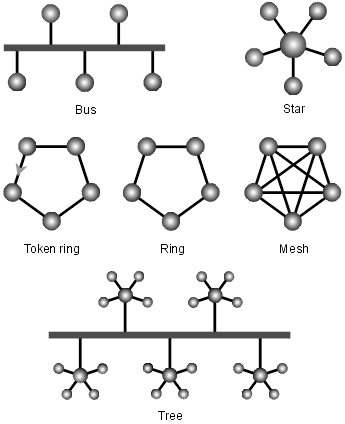 Devices
Devices
I could have just said Computers, but after thinking about servers, desktops, laptops, notebooks, palmtops, and MP3 players, where do you draw the line? What about TVs? Isn't that a TV network? And phones are on a phone network right? But if you use the phone network to connect to the internet, isn't that a computer network? If your phone is using VOIP isn't that a computer network? If you are watching TV on your PC? If your watching a TV program on the Internet? If your listening to the radio on the Internet? If you are browsing the Web over the radio? If you are using your cable modem to your Wi-Fi to do all of the above simultaneuously?!?
Ummm... okay, so it looks like all electronic devices are turning into computers and all Networks are turning into computer networks, so lets just call this component Devices to keep it simple.
Topologies
How things are connected (Daisy Chain, Ring, Bus, Star, Mesh, Hybrid, Wireless?, etc.) Wireless may not be a wired topology, but it might be still be considered a broadcast topology. Anyway, the way that the recievers are connected are still within the network topology category.
Protocols
Rules of communication (Ethernet, USB, Wi-Fi, PPP, TCP/IP, etc.).
All of these things together are referred to as the Network Architecture. That's a loose term that just means the hardware and software
Protocols
 The largest and most complicated Network Component to talk about are Protocols so lets break this down. Protocols are all over the place for everything electronic, and when looking at Network Protocols you get a series of layered protocols that are in use at different stages of sending and recieving data, so it helps to use what's known as the OSI Model to keep track of the stages.
The largest and most complicated Network Component to talk about are Protocols so lets break this down. Protocols are all over the place for everything electronic, and when looking at Network Protocols you get a series of layered protocols that are in use at different stages of sending and recieving data, so it helps to use what's known as the OSI Model to keep track of the stages.
The Layers I'll talk about here are Link, Network, Transport, and Application. OSI has 7, but I'm looking at TCP/IP, and these are the only OSI layers TCP/IP uses. The OSI thing was created before TCP/IP was, as a tool for protocol designers to help keep things talking with each other, so I'm not getting into all that, just using it to keep track of our layers.
Ethernet, Wi-Fi,and USB are hardware protocols more officially catagorized as "Data Link" protocols when using the OSI model, and so are in a different protocol category than TCP/IP. There are more hardware protocols than these, there are probably hundreds out there, but these are the most common when talking about Networks (as of 2005).
Ethernet is a marketing term used to make IEEE 802.3 easy to pronounce and recognize. It commonly works with "Cat" or catagory cables, which look like fat telephone cables. The standard Ethernet cable now is Cat5, but Cat6 is just around the corner. Ethernet has become the standard LAN protocol, but remember how flimsy the term LAN is?
DSL and Cablemodems often have Ethernet ports on them that connect to the Ethernet port on your computer (or the Ethernet port on your Wireless box, unless your wireless service is integrated). In the Office, Ethernet is king. It was designed for Computer Networks since the very early days of getting computers to talk to each other. Not long ago, if you wanted Ethernet, you would have to go out and buy an Ethernet card and install it in your Desktop or Laptop, but just about all systems today have this hardware built right into the motherboard, that's how standard it has become.
USB is another common hardware protocol you might see on your computer or your broadband internet connection. USB was designed to connect local computer equipment together like printers and drives, but it is starting to creep into network equipment. You can even find USB to Ethernet converters, in case you don't have an Ethernet port on your system, so it's understandable if you get confused by all of these protocols.
PPP is commonly used as a dial-up modem protocol, the protocol that runs the phone port that is probably already built into your system's motherboard too (although it looks like new systems are starting to drop the phone/ppp port). In the home, PPP used to be king, until broadband arrived.
Wi-Fi is a marketing term to make the IEEE 802.11 standard easy to pronounce and recognize. It's the standard for Wireless networking, and comes is A,B G and N formats.
But here comes something different, TCP/IP. All of the above protocols often carry another protocol the king of king protocols, TCP/IP.
What is TCP/IP?
TCP/IP is how the Internet delivers data. The Web, e-mail, text messaging, music, video, voice, etc. all of it is being sent and recieved by TCP/IP. Since the Internet went public, TCP/IP has become the "Network Layer" Protocol of all time. As I mentioned before, the above protocols are offically considered "Data Link" layer protocols. TCP/IP on the other hand is considered a "Network Layer" protocol.
Going to the library to pick up a book on TCP/IP is a really good idea as this is a huge topic that I am only going to scratch the surface of.
TCP/IP is a collection of 2 separate protocols, Transmission Control Protocol and Internet Protocol.
TCP is all local, meaning it all happens inside a computer. It is so different, that it is offically on another layer than IP. TCP's layer is called the "Transport" layer.
IP is all external, meaning it all happens between computers, over the network, so it's on the "Network" layer.
They were created to do different things, but when put together they solved a lot of problems. That's why it's got such a weird name and that's why you might hear it being called a protocol suite. With all these layers, you'll also hear it being called a protocol stack.
IP Addressing
IP addresses, like the computers that were used to create it, are 32 bits. They look something like this: 127.0.0.1
They are divided into 2 sections: The Network section (called a Network prefix) and the Computer section (called the Host number). This is so your message can get to the right network, then find the right computer, much like an envelope has a zip code, then goes down to the steet name and house number. But there are more than one kind of IP address.
There are 3 main IP types, divided into CLASSES A, B, and C. Class D is a special multi-cast class and I have no idea what the E Class is for.
The classes change where the division between the Network and the Host are, but they are all 32 bits total.
Class A: 8 bits for Network + 24 bits for host = 32 bits
Class B: 16 bits for Network + 16 bits for host = 32 bits
Class C: 24 bits for Network + 8 bits for host = 32 bits
Each Class also starts with a different number.
Class A: 1 to 126
Class B: 128 to 191
Class C: 192 to 223
Dot Notation: to make it easier to read, IP addresses are separated into four 8-bit fields (4*8 = 32). Sometimes you'll hear these 8-bit fields referred to as "Octets" oct is another word for 8 (latin I think).
8 bits? But IP addresses have no more than 3 numbers per dot, what gives?
Bit = Binary digit.
Binary is a number system where all values are expressed by either a 1 or a 0. Bi is another word for 2 (latin again?).People are used to using the decimal system where you have 10 [yep dec is latin for 10] values (0 to 9). At the end of 9, you move to the next placement to keep going. These placements are in 10s: 1, 10, 100, etc. Binary works the same way, but in 2s: 1, 2, 4, 8, 16, doubling forever.
For example, 10 in binary = 2 in decimal. 11 = 3, 100 = 4, 101 = 5, 110 = 6, 111 = 7, 1000 = 8, 1001 = 9, etc.
So, if IP addresses are separated into 8-bit fields, what the highest number you can get? 11111111 in binary = 255 in decimal (128+64+32+16+8+4+2+1 = 255).
Subnets
In the beginning, every host was supposed to have it's own unique IP address. At that time, no one knew the Internet would be so popular. With the huge gaps in the ABC classes, unique IP addresses were getting used up too fast, administrators had to register for another network number whenever they needed a separate network at their organization, and router tables where getting too big to manage. Something had to be done in a hurry.
The idea of breaking a network up into subnetworks became the solution. Within a single class address, apply a subnet, and you can break your network up into pieces. Why would you want to do that? Speed and manageability are the main reasons, but their are other reasons like security, safe network product & service testing, and when you change Network media, like going from Ethernet to Fiber Optic.
How do you apply a Subnet? With Subnet masks. Subnet masks tell routers where to go. Subnet masks are specially reserved numbers used to tell the router about subnets. If all bits are turned on in an Octet (decimal 255), routers skip to the next section of the address. This helps to keep router tables small and quick.
Find out more about this section from a book. Continuing on about this will drag the conversation into Routers and routing protocols and I'll get lost. Whole books out there talk about Subnets, how they work, how to plan for them, etc.
IP Special Numbers
255 is a special number, is is reserved for Subnet masks.
Some whole IP addresses are reserved for special things.
127.0.0.1 is a special number called a "loopback" that is, it's function is a loopback, but is also has a host name called localhost. All computers that use IP have this number. It is not routable, it is only used as a diagnostic test to make sure that the TCP/IP protocol is working on your system. You can use it by ping 127.0.0.1, if this ping fails, the protocol is not binding to your Network card. This doesn't involve any of your IP settings, so you can tell right away that you need to reinstall your protocol or your Network card, or replace your NIC.
There are also private network addresses. These addresses will route within your network, but not across the public Internet. There is a private address space for each IP class.
Class A = 10.0.0.0 to 10.255.255.255
Class B = 172.16.0.0 to 172.31.255.255
Class C = 192.168.0.0 to 192.168.255.255
Since these addresses are blocked from Internet use, you do not have to ask a registry service to use them.
TCP
Transmission Control Protocol uses port numbers to identify the kinds of data that pass in and out of the computer. What TCP is doing with these ports is to strip the IP (Network Layer) off and taking it up to the Application layer, which fits in with the mail clerk metaphor opening the mail package and getting the letter to it's destination. Generally there are 3 types of Ports: well known, registered and private. The most well known ports are:
Port 21 = FTP, Port 23 = Telnet, Port 25 = SMTP, Port 80 = HTTP. There are more common port mappings listed in the
Security Section.
There are thousands of available ports in TCP. I think the number was a bit over 65,000 ports. Every TCP Applcation needs a port, and unregistered applications are not supposed to be able to use registered and well known ports. It turns out that there is a big security risk with keeping unused TCP ports open on a system. It's kind of like leaving doors to the office unlocked and unattended, so one of the things a firewall does is to lock unused TCP ports and monitor the open ones. TCP is again a big area that deserves a good book, but here is an overview.
In order to make network traffic easier to manage, IP slices up the data into little pieces called packets. A packet is a data unit containing 3 sections:
- Header = address info
- Data = the info being sent, and some info on the sender.
- Trailer = checksum info, such as how many packets the original message has been broken into.
IP sends packets, which may scatter out to finding different paths to your destination, each acting independantly of each other like runners in a race to the finish line. Like a race, it is possible that the runners (or packets) will not make it to the finish line at the same time, or even at all.
Packets make it much easier for routers to run smoothly. If your message was large, and delivered all in one piece, it might take a router too long to pass it all through, causing data traffic to get backed up. Using plumbing as a metaphor, you can say that packet switching flow is like using a garbage disposal to chop your food up so that it will slip down the drain smoothly and not get stuck in the drain pipe. Network traffic flows fast and relentless like water pipes, so packets are essential in keeping things running.
The problem is that applications need every bit assembled in order so that they can read it properly. IP is considered a unreliable or connectionless protocol, as it doesn't keep in contact with the packets during their delivery, it just deals the packets out, but it makes sure that the packets have everything they need to get to their destination. These types of stand alone packets are called datagrams.
As independant as datagrams are, they can still get lost or corrupted on their path. This is where TCP comes it. TCP is a reliable protocol that collects the packets, and reads a sequence number in the packets to put them back together in order. If pieces of the puzzle are missing, TCP will wait for a preset amount of time called the Round Trip Time (RTT), then ask for them to be resent. When all the pieces are in, TCP then reads the checksum data in the packet trailer to make sure the reassembled data did not get corrupted. Once everything is in order, it passes the data to the application.
If uncollected packets were allowed to live forever, the Internet would get flooded with garbage pretty quickly, so packets have something called a time to live (TTL). It's a preassigned number, that gets reduced each time it passes though a router. Once the TTL reaches 0, the last router drops it. You can see TTL in action by pinging a computer that doesn't exsist. You ping packet goes out, then you get a report saying that the packet timed out, instead of a reply. Replys can only come back from connections that exsist.
Keeping packets flowing safely and quickly on a network is part of a Network administrator's job. If data isn't flowing like it should, Administrators can use a tool called a Packet Sniffer to help determine what is going wrong.
Packet Sniffers, also known as Network Analyzers are specialized hardware or PC based Software that reads all network traffic in it's network section or node. Most network monitors use a sniffer on a central network switch. Firewalls also monitor LAN packets, but sniffers are designed for administrators to read, usually containing analysing tools to help the administrator understand and solve various network problems.
TCP/IP Applications
File Transfer Protocol: Created before the web for exchanging files, FTP is still commonly used as it handles large file transfers quickly. FTP clients and servers often use download management features that can pause download or upload processes, allowing dial-up users to do things like talk on the phone, then reconnect and resume their file exchange where the left off from.
TELNET: Created before the web, telnet allows one computer to connect to another. Simliar to an FTP connection, but closer to a remote access connection, telnet is text only, but allows you to run programs on a remote computer. Telnet is not commonly used anymore. It is not considered secure, because the data flow can be captured and viewed by a router or similar network service like a Network Sniffer. A popular secure replacement for Telnet is called SSH, Secure Shell. It's basically an encrypted version of Telnet.
SMTP: Simple Mail Transfer Protocol: A quick text based e-mail protocol, SMTP is not just used for email, it's also by various network software to send data to other network software.
HTTP: Hyper Text Transport Protocol: Is what the Web uses to send and recieve data. The web browser makes a request to the web server, which returns the requested data back to the browser. The Data can be any type of file. The files are arranged on the browsers screen based on HTML (Hypertext Markup Language) instructions, but HTML is not required for HTTP to work. HTTP will transport just about any kind of computer data. HTML doesn't require HTTP for that matter. You can download HTML files using FTP, or any other transport protocol and display it with your browser, but the combination of HTTP and HTML using URLs is typically what is referred to as theWorld Wide Web.
HTTPS: A secure version of HTTP using SSL (Secure Socket Layer).
TCP/IP Commands
PING:
Ping is a TCP/IP command that sends a small "request for reply" to a system. Use ping to troubleshoot IP connections.
NSLOOKUP:
Find the IP address from a name, or find a name from an IP address. Example: nslookup Google.com will return something like 64.233.187.99. If more than on address is returned, it means that more than one computer it sharing that name.
TRACEROUTE:
Use this on Unix or Linux to find out what routers are being used to get you to your destination.
TRACERT:
Windows version of Traceroute, which first returns what DNS server you are using, then returns what DNS info that server has on the address or name that you entered.
HOSTNAME:
Enter hostname to resolve your computer's host name. Pinging " localhost " will also resolve your hostname. For that reason, many people forget about the "hostname" command.
ARP:
Address Resolution Protocol resolved IP addresses to NIC addresses. It's not commonly used, but if you type in arp -a, you can get a list of any cached LAN connections you have made. It will show the IP and MAC and type of address (static or dynamic). Media Access Control (MAC) addresses would typically be your Ethernet card's unique address. This has nothing to do with the Apple Machintosh.
Network Services
 DHCP
DHCP
Dynamic Host Configuration Protocol. This service automatically assigns computers an IP address taken from a pool of available numbers. DHCP makes it much easier to manage a large IP network as there is no need to assign an IP address and configure each computer in use on the network. All you need to do is configure each workstation or device to recieve a DHCP assigned IP address and configuration and DHCP will do the rest. Most Operating Systems now set their TCP/IP stack as Dynamic by default, so many users don't know what their IP address is, or ever bother to find out how IP works. Great as DHCP is, dynamic addressing is not usually used for computers that are commonly accessed by name, such as servers. Servers usually get assigned a static address to prevent problems or excess traffic with the DNS server.
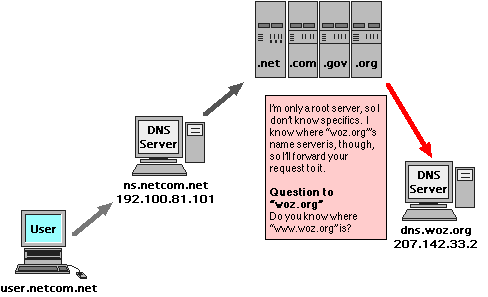 DNS
DNS
Domain Name Service. This service keeps a list of Computer names and their IP addresses. If you access a computer by it's name (such as www.woz.org as illustrated here) you are using a DNS server somewhere that translates that name to it's IP address so the router can route your request to the proper destination.
If the computer you are looking for is on the same LAN as you, then the local DNS server just answers this quickly. Either you would have entered the DNS address into your workstation, or if you are set to be dynaimic, the DHCP server will tell your computer where the DNS server is. Most of the time, these two services will be running on the same server hardware. Even in a little home network, there is software that will do this for you, either in your broadband connection box, or even built right into your Operating System.
If the computer you are looking for is on a separate LAN, things get a little trickier.
Your local DNS server doesn't keep a copy of all computer names in the world. That would just be too much work to do, and nearly impossible to maintain. What happends instead is pretty much the same situation Routers go through when they don't know where to route your data too. They ask someone else. As spread out as the Internet tries to be, there is still a bit of a pyramid structure when it comes to DNS services.
The Local DNS will ask what's known as a Root server to find the domain's DNS server wich will then direct you to the right server on it's network. These Root DNS servers are owned and operated by the places where you go to register a public network name, such as Internic. In the beginning, this was only handled by the US Government, but there are now several commercial naming service centers around to help with this task.
NTP
Network Time Protocol, which sets computer clocks over network connections. Many NTP servers exsist on the internet, and are normally used by network devices and servers to keep accurate time reporting for data synchronization and accurate log reporting.
NNTP
Network News Transfer Protocol. Used for transporting Usenet data.
Usenet
A bulletin board like message posting network. Usenet was created before the Web, but resembles a network of blogs, or a form of public emailing. Usenet access requires an NNTP server account and NewsReader client software. There are also Web based Usenet gateways, such as Google Groups, that will allow you to read and post to the Usenet, and only requiring a web browser and a connection to the free Google groups website.
Wireless
Standards:
- 802.11a = 54MBps @ distance of 50 feet
- 802.11b = 11MBps (5MBps with WEP) @ distance of 200 feet
- 802.11g = 54MBps (30MBps with WEP) @ distance of 200 feet
- 802.11n = 100MBps (not yet available)
- Bluetooth = 2MBps @ distance of 30 feet (No TCP/IP support)
- Pre-N = a proprietary way to push wireless speeds until the new 802.11n standard is completed.
Wireless Terms:
- WEP (Wired Equivalent Privacy) = early wireless encryption.
- WAP (WiFi Protected Access) = newer, better than WEP encryption.
- VPN (Virtual Private Network) = how people without WAP secure their WLANs.
- SSID (Service Set Identifier) = wireless network name that when set to broadcase just identifies itself so you can choose which wireless connection to logon to, or it can act as a password if the access box is set not to broadcast the SSID.
- MIMO (multiple-input multiple-output)= A technique for boosting wireless bandwidth and range by taking advantage of multiplexing.
Wireless Modes:
- AdHoc is a peer-to-peer form of wireless communication, allowing wireless users to talk directly to each other.
- Infrastructure has your workstation access one specific wireless access box. This box assigns your systems IP address and determines the security policy (WEP, WAP, VPN, etc).
Router
This service passes information from one network to another using a routing table. Routers are usually specially built computers dedicated to this service, but can be setup on any computer with the right software and at least 2 network cards installed.
The distinction between a Firewall, NAT, and Router shouldn't confuse you. These are just services, or things a computer can do. All of these things are often together in the same machine. They don't have to be, but they usually are. In fact, in a small office network, it's not too uncommon to have all the Network services you can think of like DHCP, DNS, Firewall, NAT, Router, and Gateway all on the same computer, lumped together with e-mail, file, and print server services.
As Networks get larger, more users are added, and traffic loads increase, you can separate these services out to among all kinds of hardware configurations. I don't even want to get into virtualization yet, but trust me, it's important to know the roles these technologies play, but the lines between them are not set in stone, and will continue change and evolve for a long time to come.
 Firewall
Firewall
This is a general term used to describe computer security. I think the term comes from another general term for the safety device in a car that protects the passengers inside the car from the heat and risk of the engine, also in a building a firewall is non flamable material that protects emergency areas like stairways.
When placed in a computer, a firewall focuses on security that allows acceptable data to enter your computer, and stops unknown data from entering. Computer firewalls are normally software that monitors what data is going in and out of your system.
A network firewall focuses on security that separates private network data from the public Internet data. Network firewalls are usually combinations of things. There are separate hardware devices that can be attached to the network to monitor network traffic like computer firewalls monitor computer data. There are also other methods that can be considered part of your network firewall such as route-filtering, NAT, Intrusion Detection and Prevention, the list goes on and on.
Because firewalls are so closely tied to computer and network security, and security is such a large issue, I've split security topics to the following page.
Click here to go to Computer and Network Security.
|
|